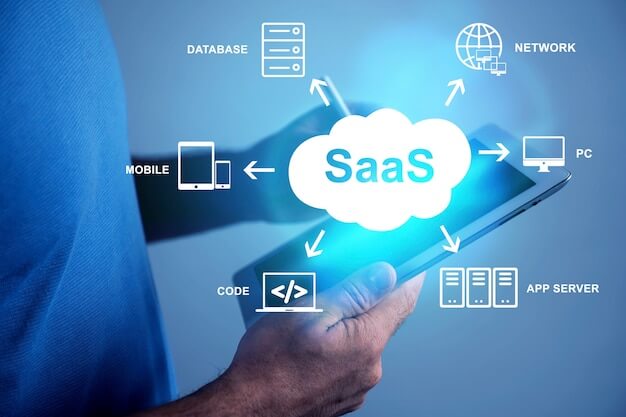
In a business environment, SaaS is an optimal alternative to local services (traditional methods), which require server creation, application installation, and configuration.
CLO
Large enterprises can no longer get away with just having local systems, moving some of their digital operations to the cloud has become necessary, and if both public and private clouds are used it is a hybrid cloud.
Cloud computing has revolutionized IT infrastructure, eliminated hardware and software costs, and allowed customers to access these resources through the Internet. Cloud computing resources include physical and virtual services, applications, data storage, development tools, artificial intelligence services and virtual machines.
The approach to cloud governance varies by domain and organization. For organizations choosing cloud computing, a thorough assessment of business macros, resources on hand, and people skills must be conducted, which are key factors that will impact a seamless and successful migration.
When the core of cloud computing system computing and processing is a large amount of data storage and management, the cloud computing system needs to be configured with a large number of storage devices, then the cloud computing system is transformed into a cloud storage system
What is clear is that cloud computing is accelerating faster than predicted, adoption rates are high, and revenue generation is soaring.
Nowadays, enterprises are more and more inclined to take data as the driving force, because their data is the driving force for their development engine to create new products, surpass competitors and provide customers with better experience. Therefore, big data management and processing for different partners (such as data analysts, data engineers, and data operating companies) should be fast, automated, and scalable.
Whether it is a public or private cloud, the intended value of the cloud can only be realized if it is used wisely. To make use of cloud computing IT infrastructure more "green", the following seven aspects are very important.
As enterprise IT operations are gradually going to the cloud locally, they begin to look for security access control methods to introduce cloud operations from internal data centers. Cloud Access Security Proxy (CASB) is such a tool. This article will take you to study CASB and explain its origin and evolution.
Serverless is a new cloud computing paradigm that allows developers to focus more on application development and deployment without focusing on the underlying infrastructure.